 These instructions will help you install the privacy-focused ChatSecure messaging app on Android and iOS-based phones.
These instructions will help you install the privacy-focused ChatSecure messaging app on Android and iOS-based phones.
ChatSecure allows you to send messages to friends as rapidly as text messages, but with the important benefit of strong encryption that prevents anyone from eavesdropping on the conversation: only you and the recipient can ever read the messages, and the conversation is effectively erased when it is closed. Regular text messages (SMS), on the other hand, can be read by the telecommunications provider (e.g. AT&T, Verizon, T-Mobile…), by law enforcement without a warrant, and potentially by anyone intercepting your data traffic. This is true even if you “delete” the messages from your phone.
In slightly more technical terms, ChatSecure is an XMPP/Jabber messaging client that implements Perfect Forward Secrecy (PFS) and Off-The-Record (OTR) communication over end-to-end encrypted WiFi or 4G/3G data channels. Here is how it works:
A unique encryption key is generated at the beginning of every chat session, and old keys are never re-used. Even if a previously used key were compromised, it would pose no risk to future communication, which would use a different key (PFS). Because nobody can prove what was discussed—not even the participants—the OTR protocol grants plausible deniability in addition to end-to-end encryption. This method is one of the safest ways to communicate digitally.
By contrast, PGP/GnuPG encrypted emails are protected using the same strong encryption algorithms, but they rely on the same key for every message (no PFS). Thus, a compromised secret key would allow the interloper to decrypt all past messages. Nonetheless, PGP/GnuPG is still an excellent method when both parties are educated in good security practices such as fingerprint verification. ChatSecure provides rapid communication, multiple levels of security, and plausible deniability not offered by PGP/GnuPG.
Configuration Instructions
1. Select ChatSecure from your list of apps after installing it from the Google Play Store or F-Droid Repository.
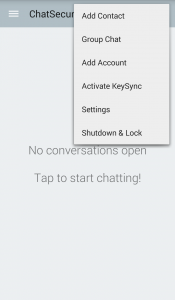
2. Tap the three dots and “Add Account.”
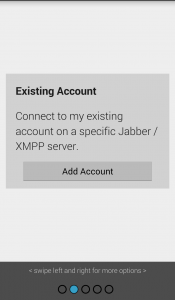
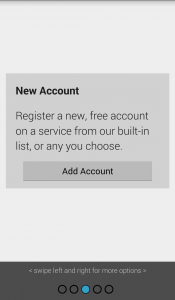
3. Swipe until you see “New Account” and tap “Add Account,” unless you already have one. For privacy reasons, I do not recommend using a Google account, but this is an option, as are other similar choices. Instead, let’s start by making a new account.
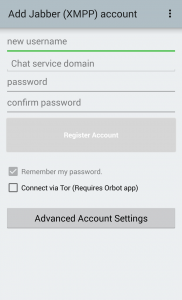
4. The account creation page will appear. Enter a new username. When you select “Chat service
domain,” a dropdown list of XMPP chat service domains will appear. These are all highly
reputable services, so unless you have a strong preference, choose whichever one you like. Enter a strong password and tap “Register Account.”
- You will not need to configure Advanced Account Settings, so ignore that.
- If you run a rooted Android phone and use Orbot, you can proxy ChatSecure through Tor. Otherwise, leave the “Connect via Tor” box unchecked.
5. Back on the main screen, tap the three parallel white lines ≡ in the top left corner of the screen
to reveal the account preview window. Tap your account name to bring up the sign-in page and
enter your username and password.
- In this example, I am connecting through Tor. If you left the Tor box unchecked earlier,
also leave it unchecked here.
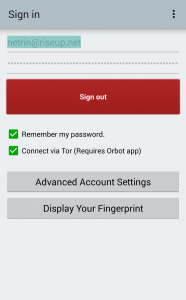
6. Once you are signed in, return to the sign-in page and tap “Display Your Fingerprint” to
generate a scannable QR Code containing your XMPP username and fingerprint. Other
ChatSecure users can scan your QR Code to connect with you on ChatSecure.

- If you do not already have the Barcode Scanner app on your smartphone, you will be
instructed to install it—simply follow those directions.
- Ideally, exchange QR Codes with friends in person for greater assurance that you’re
connecting to the intended recipient.
- Otherwise, upload your QR Code to a secure image-sharing site like https://img.bi/ and link your friend to it.
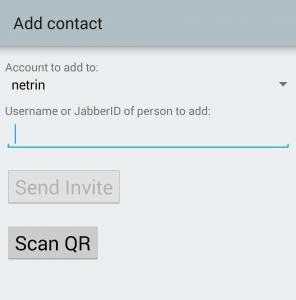
- If you do not have a contact’s QR Code, you may still be able to find them by selecting “Add Contact” and searching for them by username. To confirm the identity of the recipient, have them read you their fingerprint over the phone while you compare it to the one displayed on your screen (or coordinate by signed email). If it is not identical, then someone may be attempting to tamper with your conversation.
7. Your chats will use the OTR protocol with encryption forced and required either over WiFi or the 4G/3G data channel. Enjoy!
- You can use Pidgin with the OTR plugin on your desktop to communicate with ChatSecure users as well.
 The Electronic Frontier Foundation’s Secure Messaging Scorecard evaluates popular communication apps based on privacy and security criteria and determines which are the best to use. You’ll quickly notice that Google Talk, AIM, and similar options are among the least secure, and it will explain to you why.
The Electronic Frontier Foundation’s Secure Messaging Scorecard evaluates popular communication apps based on privacy and security criteria and determines which are the best to use. You’ll quickly notice that Google Talk, AIM, and similar options are among the least secure, and it will explain to you why.












